01. Introduction
There is a general documentation available for the EBF Onboarder, where you can find information about its prerequisites and the whole migration project. It describes how you can setup a migration project, how you can setup invitation emails and reminders which guide your users through the migration. It also tells you how to initiate the migration process and how to track the migration status.
This documentation complements the general EBF Onboarder documentation and provides more detailed information for the target system Microsoft Intune about:
- the prerequisites for the target system,
- the target system selection and setup during the migration project setup,
- the device selection during the migration project setup,
- the monitoring of the migration project.
| The EBF Onboarder supports the following endpoints (National Clouds) offered by Microsoft: | |
| Global Service & GCC [DEFAULT]: Select this option if you use the standard Microsoft Azure/Intune system with Azure AD endpoints: |
US Government L4 (GCC High): Select this option if you use the Microsoft 365 L4 GCC High environment with the following Azure endpoints to connect to your system: |
| China operated by 21Vianet: Select this option if you use the Microsoft Cloud for China operated by 21Vianet environment with the following Azure endpoints to connect to your system: |
US Government L5 (DoD): Select this option if you use the Microsoft 365 L5 DoD (DoD=Department of Defense) environment with the following Azure endpoints to connect to your system: |
| German Cloud [DEPRECATED]: The German Cloud reachable at https://portal.microsoftazure.de is out service. |
|
02. Prerequisites for the target system Microsoft Intune
NOTE:
We already inform you our FAQ not to add more than 1000 devices into one project, we also ask you not to start the migration of more than 4000 devices a day because of Microsoft Azure Graph API limitations. Delays while adding a device to the corporate device group or adding user to a group might occur.
NOTE:
Please check chapter 4.3.2. to get more details about Apple ADE/DEP and User Enrollment in an UEM/MDMs, chapter 4.3.3 for more details about Android Devices.
02.1. Microsoft Intune Service Account
We recommend creating your own Microsoft Azure app that allows the EBF Onboarder to access your source system and to have control over the app and client permissions (see chapter 02.1.1). The setup is the same for each endpoint/region.
Otherwise you can also use the EBF Onboarder and its shared app (see chapter 02.1.2).
ATTENTION:
- The EBF Onboarder will not support Multi Factor Authentication (MFA) for the Intune Service Account as API requests of the EBF Onboarder do not support Multi Factor Authentication or Single Sign On (see chapter 02.1.2).
- But you can use Multi Factor Authentication for your users. The EBF Onboarder is able to migrate devices if you use Multi Factor Authentication and the Microsoft Company Portal will accept the user credentials with MFA (security reinforced) during registration.
02.1.1. Using your own app (recommended)
We recommend using your own Azure app instead of the EBF Onboarder shared app!
While creating the app in Microsoft Azure, you will get the Directory (tenant) ID, the Application (client) ID and the value of the client secret. You will need three values to configure your EBF Onboarder projects.
First you need to clarify (relevant for step 2): Which ownership should the devices have in Microsoft Intune?
- Corporate only
- Personal only
- Corporate and personal devices
Follow these steps to create the app:
01. Create your own app for the EBF Onboarder:
- Login into the Azure Portal (Default: https://portal.azure.com/).
- Within ‘Home’ and ‘Azure services’ click on ‘App registrations’.
- Register a new app by clicking on ‘New registration’.
- Enter a user-facing display name.
- For ‚Supported account types‘ select ‚Accounts in this organizational directory only (Single tenant)’ and click on ‘Register’:

- You will find your Application (client) ID and Directory (tenant) ID on the next page. You can copy them now and also look up these information at any time within the app in your Microsoft Azure tenant.
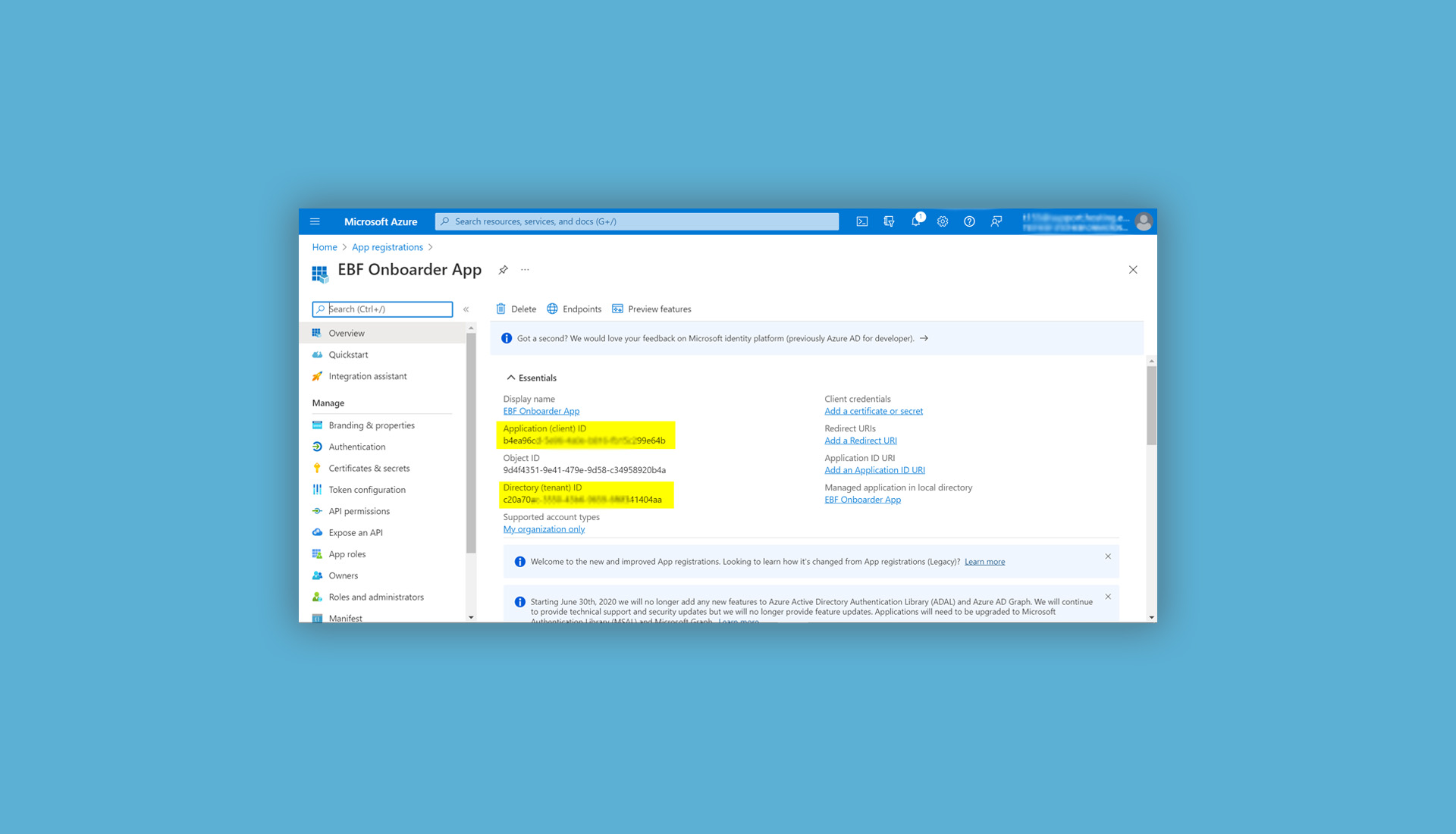
02. Go to ‘API permissions’ on the left side on the same screen:
- delete the existing permission ‚User.Read’ and confirm (press the three dots, click on ‘Remove permission’ and confirm with ‘Yes, remove’)
- click on ‘+ Add a permission‘ and select ‚Microsoft Graph’,
- select ‘Application permissions’,
- add the following permissions for the Service Account (follow the information which correspond to your device type) and press the button ‘Add permissions’:
Please add the following permissions for corporate devices only:- User.Read.All
- Directory.Read.All
- Device.Read.All
- DeviceManagementManagedDevices.Read.All
- DeviceManagementConfiguration.ReadWrite.All
- DeviceManagementServiceConfig.ReadWrite.All
- Group.ReadWrite.All (only necessary if you want to add migrated users to a group)
Please add the following permissions for personal devices only:
- User.Read.All
- Directory.Read.All
- Device.Read.All
- DeviceManagementManagedDevices.Read.All
- DeviceManagementConfiguration.ReadWrite.All
- Group.ReadWrite.All (only necessary if you want to add migrated users to a group)
Please add the following permissions for a mix of corporate and personal devices
- Configure the app registration for personal devices.
For devices with corporate ownership in Microsoft Intune you need to import the Serial Numbers or IMEIs into Microsoft Intune BEFORE the devices migrate. See ‘Microsoft Intune > Home > Devices >Device Onboarding > Enrollment’ for more details. - Or: Setup groups on the source system which contain either the corporate or the personal devices only. Setup the app registrations for each type (see above) and use them in these projects only.
NOTE: In case there are issues with the Read-only permissions, we recommend using ReadWrite permissions:
- User.ReadWrite.All
- Directory.ReadWrite.All
- Device.ReadWrite.All
- DeviceManagementConfiguration.ReadWrite.All
- DeviceManagementManagedDevices.ReadWrite.All
- Group.ReadWrite.All
Minimum /No permissions:
There might be cases where security teams do not allow these permissions. But we need the permissions above to fulfill all the features available by the EBF Onboarder.The absolute minimum set of permissions are:
- Directory.Read.All
- DeviceManagementManagedDevices.Read.All
- For all cases: ‚Grant admin consent for (your domain)’.
03. Go to ‘Certificates & secrets’ and set up a new client secret:
- Press ‘+ New client secret’, provide a meaningful description and select a value for ‘Expires’. It would be possible to choose the planned migration date, but it is recommended to add some months to be prepared for a possible delay.
- Press ‘Add Copy the Value’ and save it at a save place as it will never be displayed again!

04. While configuring the migration project with the EBF Onboarder
you will be asked to define the target system, the National Cloud type and to insert your tenant ID. After entering the tenant ID, the form will switch to ask you for the client_id (Application (client) ID) and client_secret (Value of the Secret) which you have received after creating your own app in the Azure Portal:
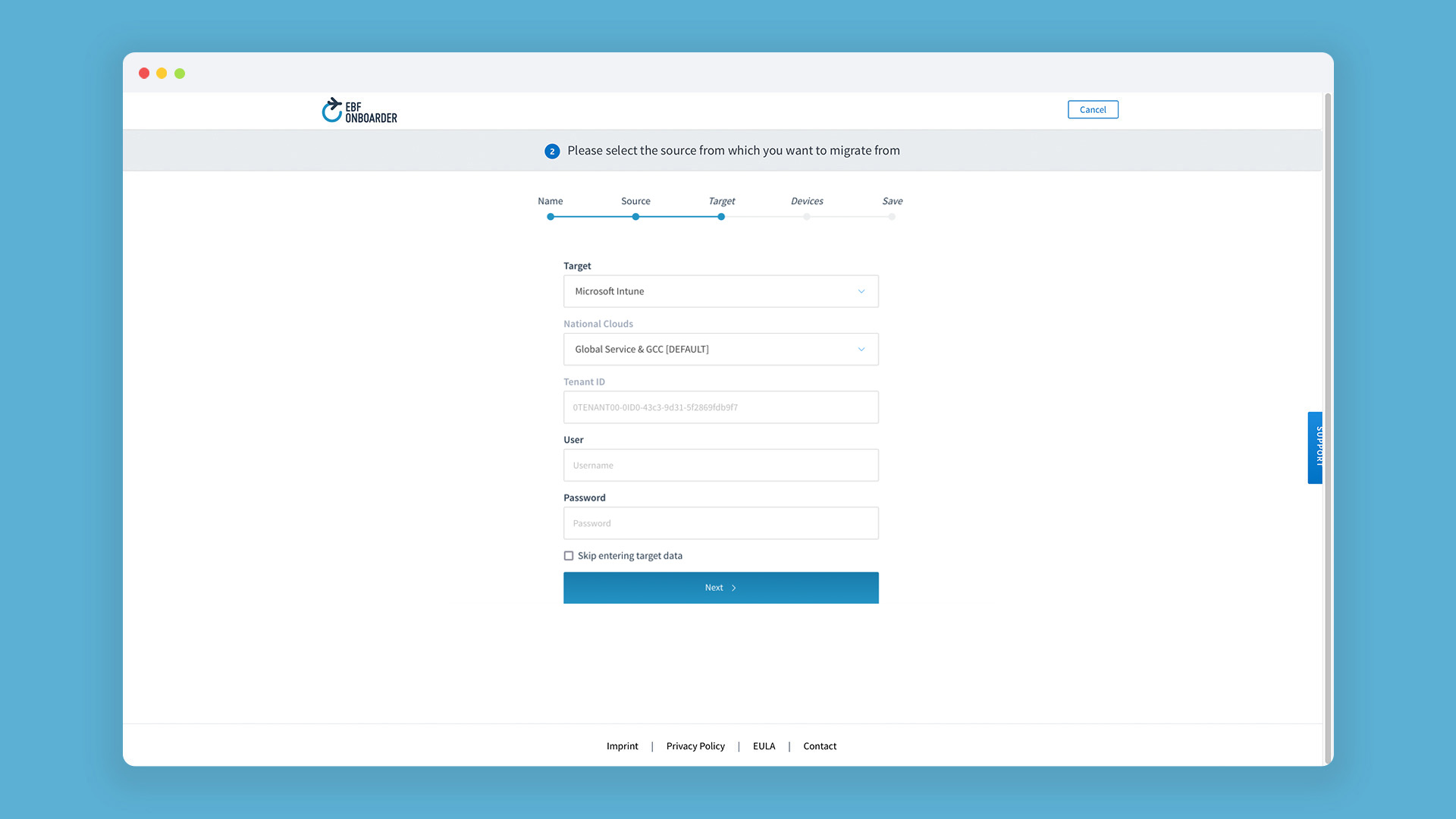
No Permission:
If you do want to use no permission at all, you can use the options “Skip Entering Data” in the Intune target setup. In this case, the EBF Onboarder will only send an unenroll command to the device (according to the source setup). The EBF Onboarder will not be able to confirm devices in the target.
07. Web based enrollment
Follow these steps to enable the web based enrollment into Microsoft Intune:
-
- Go to ‘Settings’ > ‘Tenant Settings’.
- Select the check box for: ‘Use web based enrollment for Intune’.
- Press ‘Save Settings’.
NOTE:
Please note that you need to configure Microsoft Intune to enable web based enrollment and check the following website for further information:
Set up web based device enrollment – Microsoft Intune | Microsoft Learn
