Security Policies, AppConnect and Restrictions
With this feature client/dept admins the content of Security- and AppConnect Policies and Restriction Configurations can be displayed, single settings can be changed and reports can be created.
The values used by MI Core can be customized and renamed.
The customized names are displayed in MIDA and in the reports.
Requirements
MIDA is created to allow client-based administration. Different clients are applied to different labels.
To properly manage the different clients, the client labels and policies and configurations must have same Labels names. An idea is to start each object with a four characters code.
The names of each Policy and Configuration needs to follow naming convention.
The following example shows the setup of a Security policy for one client.
Client Label: DEMO_Corp
Name of Security Policy: DEMO_SecPol1
Open Settings > Policy Sync Config > Actions > New Policy Sync Config
Name: SecPol1
Name Pattern: {{first4LabelChars}}_SecPol1
Policy Type: SECURITY_POLICY
Copy Fields from: Select the Policy Sync Config to copy the Fields configuration from any other policy.

Open the SecPol1 Sync Config.
Press the refresh button to pull all available parameters in a security policy from the MI Core.
Note:
MIDA will create a policy “MIDA Technical SECURITY_POLICY” on the MI Core, pull the available parameters from this Policy and delete it afterwards. Equal temporay objects will be created for AppConnect und Restrictions
The parameter iPhone (Min iOS Version) is always added for a Security policy, but can be removed.
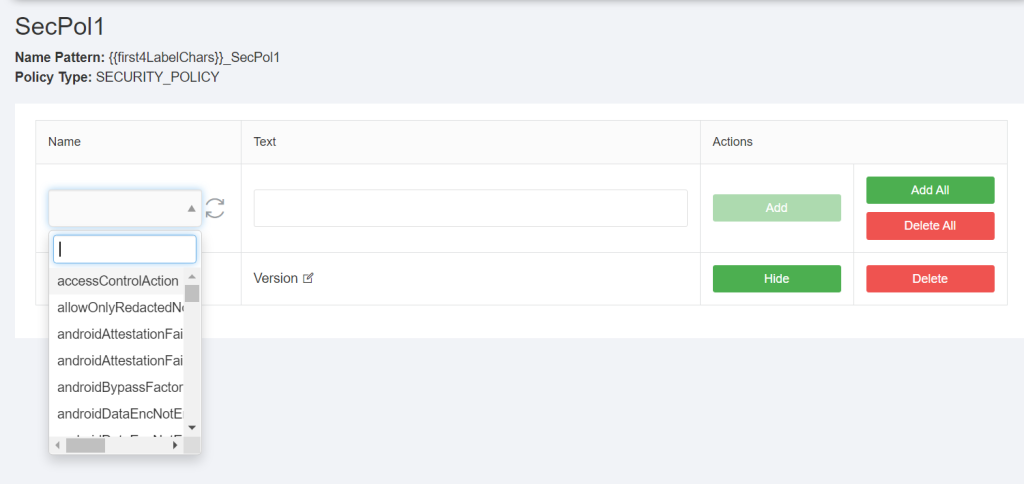
You can either use the “Add All” button to add all parameters of the Security policy to this configuration or use the name filed to search for single parameters.
The selected parameter will show up in the name field. You can now enter text of your choice for this parameter. If you do not enter a text and press Add, MIDA will use the parameter as text. It is recommended to add a user friendly text for each parameter.
Changes/Edit
- The Hide button in each line can be used to hide this parameter from the Policy and Configuration and Reports but to keep the text in the system
- Press the Show button to display it again.
- Press the edit icon in the text column of the parameter to edit the text.
- To reset the whole form press the “Delete All” button.
- Using drag and Drop you can change the order of the rows. To confirm drag and drop changes use teh Save button to configm the changes.
A MIDA client admin can add this Policy in “Policy and Configurations” > New Policy:
The Name of the policy will be displayed in a drop down list and can be selected and added.
Note:
Changes in the Poilcy Sync Config will show up right away in the policy if refreshed.
If the Policy was added by the client admin and corresponding Config is deleted, the policy is no longer available for the client admin.
Policy Sync Configs for App_Connect and Restrictions are created in an equal way.
The required permissons:
The Policy Sync Config is configured by the Superadmin or a Superadmin-like user in the MIDA Settings. A Superadmin-like user needs the following permissions:
To setup the Policy Sync Configs(if not setup by the MIDA superadmin)
Policy Sync Config Field:resyncAvailablePolicyFields
Policy Sync Config Field:findAll
Policy Sync Config Field:findOne
Policy Sync Config Field:delete
Policy Sync Config Field:save
Policy Sync Config Field:deleteAll
Policy Sync Config Field:addAll
Policy Sync Configs:Delete
Policy Sync Configs:Findall
Policy Sync Configs:Save
MIDA client admin:
Required to use the Policy, change the iOS Version in a Security Policy and create Reports:
policies:findOne
policies:findAll
policies:sync
policies:create
policies:availableIPhoneVersions
policies:editIosVersion
policeis:findIosVersion
policies:delete
reports:securityPolicy
reports:appConnectPolicy
reports:restrictionConfiguration
Set the Minimum iOS Version
Using the menu item Policies and Configurations > Security Policy the minimum iOS version of the iOS devices for Security policies can be adjusted for the devices of a mandate.
If a policy created by a Policy Sync Config is added by the MIDA client admin, MIDA checks the MI Core in regards to the name pattern of the Policy Sync Config and stores the object ID of the Core for the further functionality. If the object is found, MIDA shows a check mark.
If the object with this name is not found, a red x will be displayed.
If the iOS Version check is disabled in a Security Policy MIDA will show:
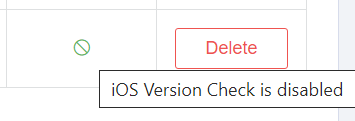
In a Security Policy the parameter iphoneOS enabled this feature.
Open the Security Policy and the parameter will show the current iOS version. Using the Refresh button the Security Policy on the MI core can be checked again.
With a click on the Drop down, the current available iOS Version on the MI Core are displayed.
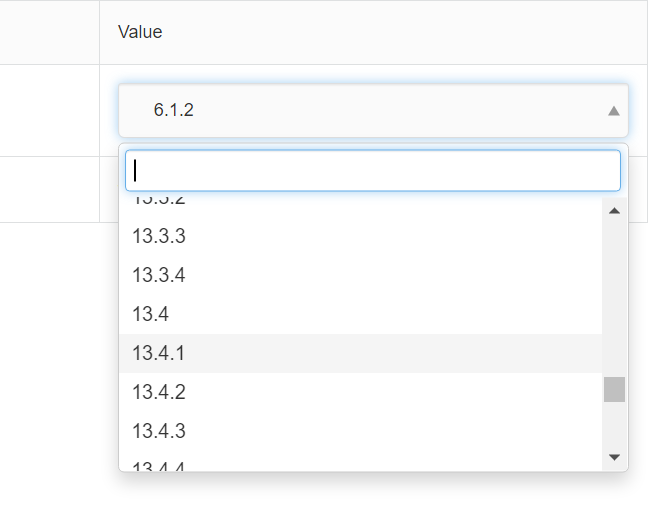
If an iOS version is selected here, a pop-up appears asking whether the iOS version should really be changed in the Security Policy on the MI Core.
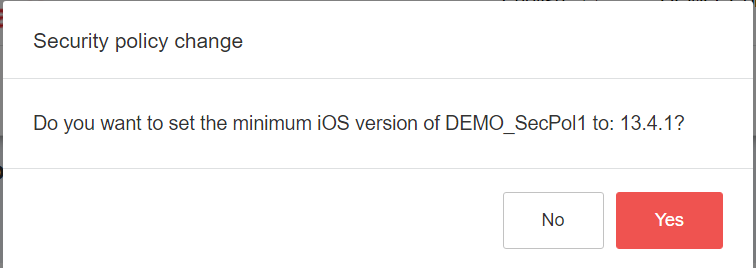
If this question is answered with „Yes“, the new iOS version is written directly to the policy on the MI Core and thus activated for the iOS devices, that are applied to the Security Policy by a label.
Defer Software Updates
The parameter Defer „Software Updates“ and the days in a Restriction Configuration on the MI Core can be set using MIDA.
Open „Polices and Configurations“ > tab „Restriction Configurations“. Select the Restriction, scroll to the „Defer iOS Software Updates“ setting:

Select true from the dropdown and MIDA will ask how many days you want to set:

For the days, according the rules on the MI Core you can set up to 90 days.
0 or more then 90 days cannot be set and will be rejected by MIDA.
After setting the days and press Save, MIDA will show a confirmation box:
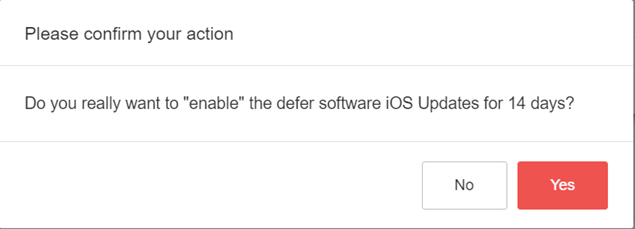
What will happen on the MI Core in the Restriction Policy:
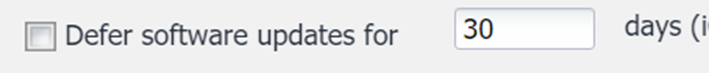
After saving the change:

Prerequirements for this feature:
- A proper setup of a Restriction Configuration in the Policy Sync Configs that includes the parameters:
forceDelayedSoftwareUpdates
enforcedSoftwareUpdateDelayThe text that will be showing in the confirm popup are the texts that are set fo these parameters in the refering Policy Sync Config. - A role, that is applied to users who should be able to change this setting, requires the permission:
policies:editRestrictionConfigs
