Actions configuration
When opened, the current compliance actions are displayed, including the executed action. These can be created, edited or deleted here.
Rebuild
- Click „New Compliance Action“.
- Assign a speaking name.
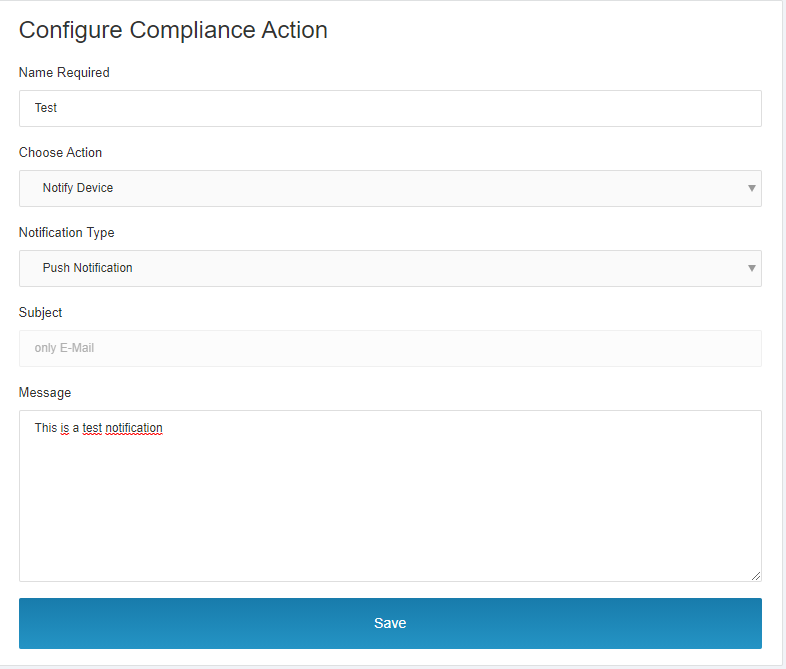
This compliance action can then be used in Black and White-App Lists.
Possible measures
Block Device
- Effect: ActiveSync and AppTunnel functions are blocked directly.
and/or:
Notification
- Through Apple Push Notification(iOS) / GCM (Android) service with a predefined text
- SMS to the device
- Email to the user
- Email to another address
Several compliance actions can be combined in one App List.
Edit / Check
- Click a compliance action to start the edit mode.
- Make changes, check and save.
Via the X in the upper right corner you leave the editing mode without saving the changes.
A compliance action can be deleted via the trash can icon in the overview.
Parameterize compliance message
Messages (not the subject!), can be provided with the following parameters to include details about the violation in the message:
- {{app}}
displays the bundle ID of the app - {{device}}
displays the MDM internal device code(uuid) of the device - {{appList}}
Displays the name of the app list
Example of parameterized e-mail
You could use the following email as an example of sending email to an administrator
use
Device: https://mida.emm/#/devices/{{device}}
App: {{app}}
Violation of App List: {{listName}}
If you are already logged into MIDA in your default browser on the desktop, clicking on the device link will directly open the device concerned.
If a device violates a black or white app list by installing an app, the device will show:
Blacklist: Prohibited App Policy has been violated.
Whitelist: Allowed app policy was violated.
For Compliant, a red X is assigned to the device. The MIDA Admin can check which app triggers the violation by opening the App tab in the Device Details.
The offending app will be highlighted in red.
About the MIDA Compliance Check Architecture
Introduction
The MIDA Compliance Check is a background process for a MIDA instance that determines the inventory of devices against MIDA app lists.
Its goal is to find unauthorised apps on devices and perform configured actions when such apps are found.
This chapter describes in detail how to perform the MIDA conformity check.
Technical architecture
The MIDA Compliance Check runs in the same process as the MIDA REST API and is executed by the Spring Task Scheduling /Execution mechanism.
In a system with multiple MIDA servers, a lock system is used to prevent running with the same data.
Stacked design
The compliance check is performed throughout the day.
The scan is performed by two separate repetitive tasks. One task is named AppHound, the other is AppPoliceman.
Both tasks use batched execution. When a task starts, it first reads a configurable amount of data (e.g. an app list) from the database. The details of the app list are read out and the position at which the data was read out is marked. At the next start, the previously processed data is read, the value is increased by one to process the next data set (app list). If increased number is greater than the number of all data records (App Lists), the counter is set to 0 again and works its way through the App Lists from the beginning again. In this way, the App Lists are processed several times throughout the day. The interval between the batched executions is configurable. The default values are: Every 5 minutes for the AppHound, every 2 seconds for the AppPoliceman.
App Hound
The AppHound task is responsible for scanning the app list table to check which devices violate an app list. The result of this task are, in case of violation, violation entries in the table „violation_record“.
The procedure is as follows:
- Take an app list from the database
- Load devices from the MI Core that are assigned to the App Listen Label
- The following procedure is repeated for each device found:
- Load the apps installed on the device
- Check the installed apps for the apps in the app list depending on the list type
- Create entries for the device in the violation_records table in case of violation
- Confirm the existing records in the database if necessary
- Proceed to the next app list
App Policeman
The AppPoliceman task is responsible for scanning the violation_record table. A compliance action is executed in the event of a violation.
If the device no longer violates the app list, the entry in the table, which is therefore no longer correct, deleted and actions, such as BLOCK, reversed (for example, to allow access again).
The following procedure is used here:
- Read Violation entry from the database
- Check the Violation if it is still valid
- Check if the Violation should be executed (There is a parameter for this so that users do not get too many messages during the day)
- If the Violation should be executed
- Ensures that the Violation entry remains
- Do not execute if messages have already been sent
- If the Violation is no longer valid:- Undo previously performed actions (e.g. BLOCK device)
- Delete Violation entry